increase an attackers cost for adding, destroying or manipulating votes.
Everyone will be able to download a list of legitimate ballots and check a ballot against it for authenticity.
Hashing is a technique from computer science and can be performed on data to produce a fingerprint of it.
A unique Hash is derived from every ballot at the time it is printed. The hashes, that represent a compressed list of legitimate ballots, are then made publicly available. In combination with Competitive Counting and Transparent Transfer one will also be able to check online and in real-time
- if a ballot has been counted, as well as when and by whom and
- for counts and progress without having to rely on the media for reporting.
This is all possible without compromising the secrecy of the ballot.
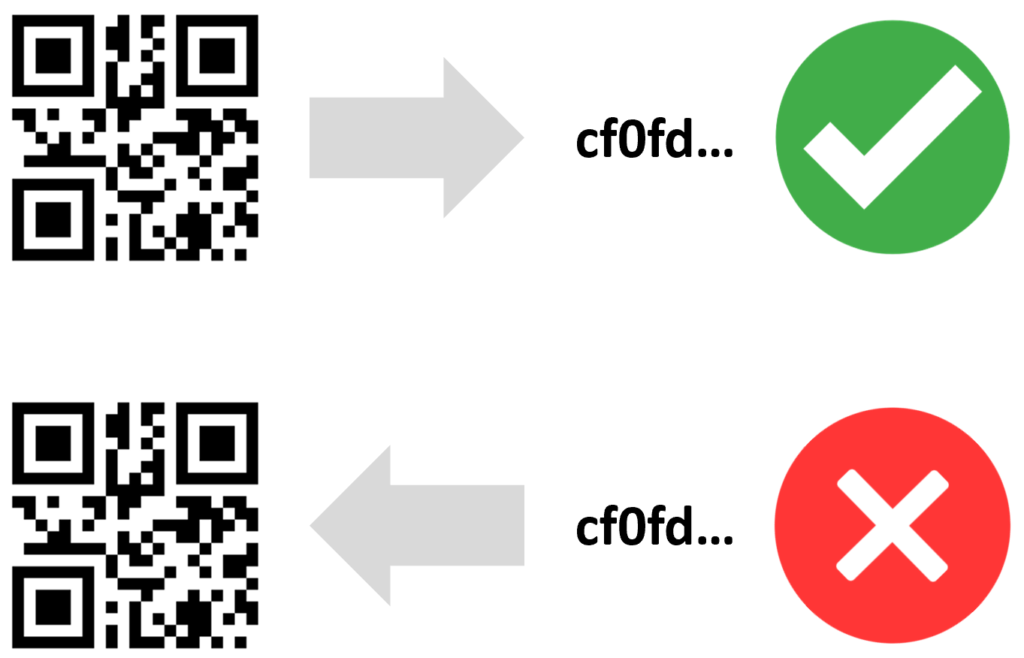
A hash acts as a valve that allows in one direction but not the other: You can link data towards the hash, but not the hash back.
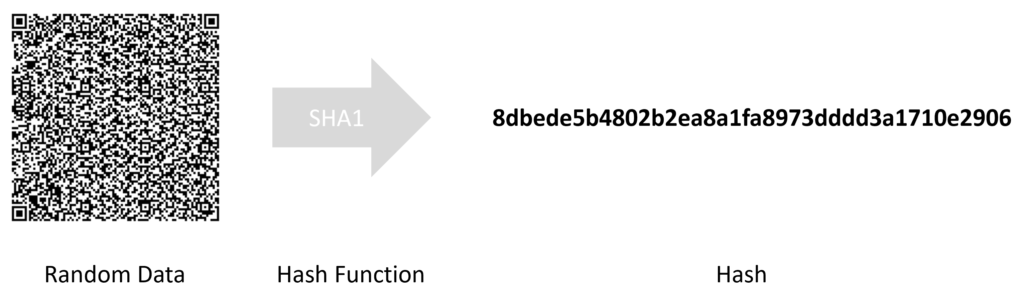
A ballot can be upgraded to a Hash Ballot by simply printing random data on it via e.g. a QR Code.

This random data needs to be reliably forgotten by the printing company the moment it has been printed on the ballot. Yet the hashed values of these need to be recorded and then published to the public.
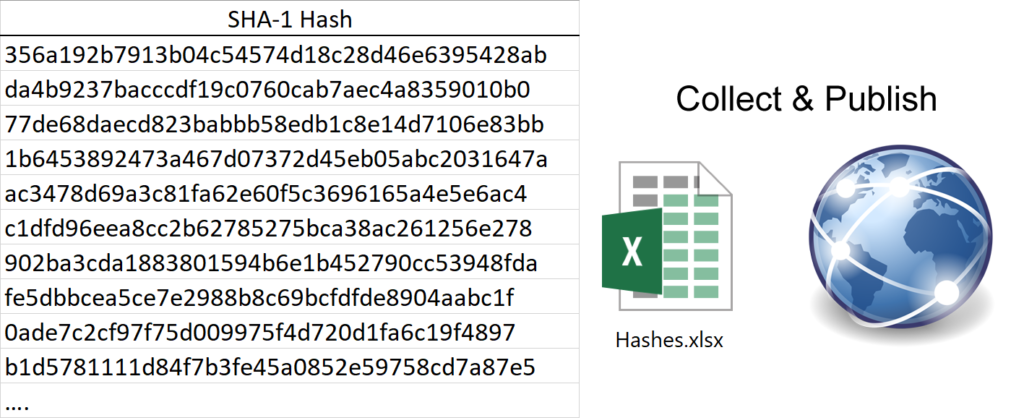
Every ballot has now become unique and traceable. Yet it can not be traced back to the original voter - which upholds the secrecy of the ballot.
Ballots can be verified by poll workers with specialized scanners for e.g. mass verification, or by poll watchers via smartphone apps. An audit can be performed on a large amount of ballots in a very short period of time.
Notes
Hash Ballots concentrate a lot of risks that are usually distributed along the processing chain towards print time. If security here is proper, the overall likelihood for fraud is reduced. Yet if it’s compromised there, any potential gains are erased.
Angles of attack
1. Siphoning original ballot data at print time (New + Critical)
It must be ensured that the original data is reliably forgotten once the ballot is printed.
2. Adding false hashes to the database at print time (New + Critical)
Checks must be present that the hashes of printed ballots & their amount is identical with database entries.
3. Swapping legit vanilla ballots with bogus ones (Existing + Critical)
Controls must be present that once printed, ballots are protected from unauthorized access.
4. Stealing filled-out ballots, then manipulating or replacing them (Existing + Medium)
Due to the neccessity to recreate each ballot individually, the cost for an attacker has significantly risen.
5. Calculating original data from the Hash (New + Very Low)
This is an attack on the hash algorithm: It is extremely costly and therefore unfeasible on a larger scale.
6. Injecting new made-up Ballots (Existing + Very Low)
This becomes unfeasible as hashes would not be in the published database: They can be thrown out quickly.

